The CISO's Relationship with Technology In the Era of Quantum & AI
- Hillel Kobrovski

- לפני 5 שעות
- זמן קריאה 2 דקות
The CISO's Relationship with Technology In the Era of Quantum & AI

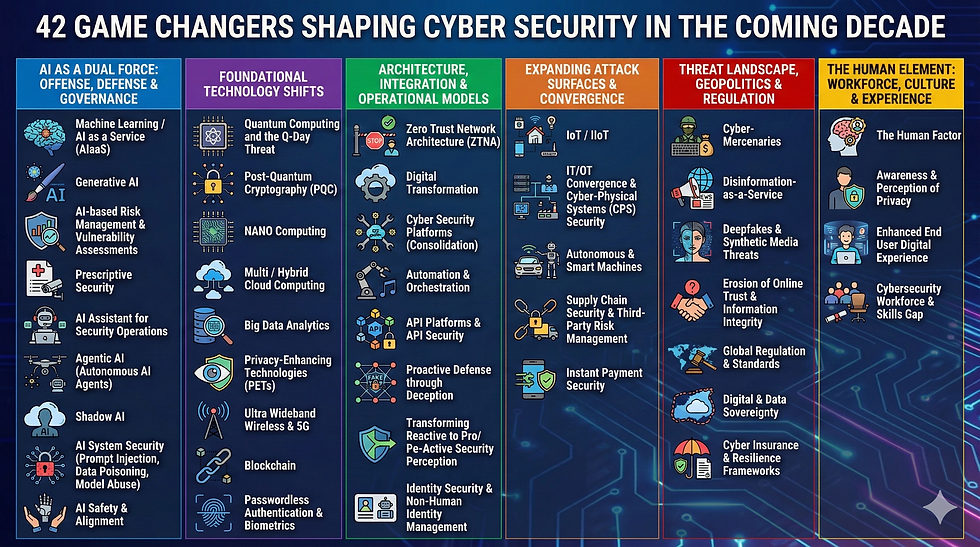
1. Hardware & Infrastructure
Hardware Security
Infrastructure & Physical Security
Wireless Security (5G/Cellular)
Secure Networking (WAN/LAN/WLAN, Micro-Segmentation, Zero Trust)
Network Security Architecture (CASB, SASE, CNAPP, SD-WAN)
Data Center Security
OS Security (Win/Linux/MAC)
OT/ICS/SCADA & Cyber-Physical Systems (CPS)
IoT/IIoT/IoMT Security
2. Software & Application Security
Public Cloud & SaaS Security
Application Security (WAF, WAAP, API Security)
Database Security
Software Development Life Cycle (SDLC)
DevSecOps & CI/CD Pipeline
Open-Source Security
Vulnerability Management & Penetration Testing
Software Supply Chain Security
Quantum Computing & Post-Quantum Cryptography (PQC)
Blockchain & Distributed Ledger Security
3. Identity, Data & Privacy
Identity & Access Management (IAM)
Privileged Access Management (PAM) & Secure Remote Access (SRA)
Identity Threat Detection & Response (ITDR)
Data Protection (Encryption, Backup, Replication, DLP)
Endpoint Protection (EPP, EDR, XDR)
Mobile OS Security (Android, iOS)
Privacy By Design & Security By Design
Information Security Regulation & Frameworks
Privacy Regulation (GDPR, CCPA, Tikon 13)
4. Detection, Response & Operations
Security Operations (SecOps)
Network Operation Center (NOC) & Security Operation Center (SOC)
DNS Security (DGA, DNS hijacking, DoT, DoH)
Email Security (Anti-Phishing, DMARC, SPF, DKIM)
Digital Forensics & Incident Response (DFIR)
IR Management & Metrics (MTTD, MTTA, MTTR, MDDR)
Threat Intelligence (CTI) & Dark Web Monitoring
Continuous Threat Exposure Management (CTEM)
Attack Surface Management (ASM)
Disaster Recovery & Business Continuity (DR/BC)
5. Governance, Risk & Strategy
AI Governance & ML Security (AI/ML, Private LLM, AIGC, Shadow-AI)
Technology Risk Assessment
Product Compliance & Industrial Standards
Supply Chain Regulation & Management
Financial Metrics & Board Reporting (ROI, TCO, OPEX/CAPEX, SLA)
GRC Platforms & Compliance Management
Security Awareness Training & Human Factor

Hillel Kobrovski, Last Update: 21.02.2026



תגובות